TL;DR – EAP-TLS Wi-Fi Authentication in a Nutshell
- EAP-TLS provides strong mutual authentication using client/server digital certificates.
- The process includes a multi-step handshake to establish a secure session.
- Key vulnerabilities include username disclosure and weak certificate validation.
- Misconfigured devices are more often exploited than the network infrastructure.
- Rogue networks can impersonate known SSIDs to launch MitM attacks.
In our previous post, we discussed various authentication methods for enterprise Wi-Fi networks. Today, we’re focusing on EAP-TLS (Extensible Authentication Protocol - Transport Layer Security)—one of the most secure 802.1X authentication methods available. We’ll break down how it works, explore key vulnerabilities, and show how attackers can exploit misconfigurations in real-world scenarios.
What is EAP-TLS? Quick Recap of the Protocol
EAP-TLS enforces mutual certificate-based authentication, requiring both the client and the server to verify each other’s identities using trusted digital certificates. This makes it significantly harder to impersonate a legitimate device or access point compared to methods like PEAP or MSCHAPv2.
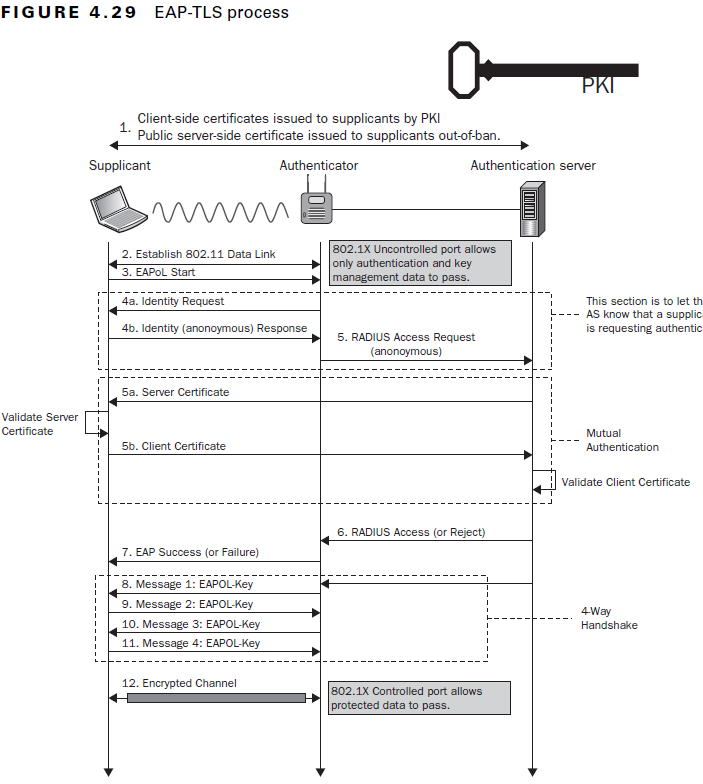
EAP-TLS Authentication: Step-by-Step Breakdown
-
EAPoL Start
The process begins when the Supplicant (STA) sends an EAPoL-Start message to the Access Point (AP), which initiates communication with the RADIUS server. -
Identity Request
The AP requests the client’s identity, usually returning a username or hostname. This identity is forwarded to the RADIUS server as part of the access request. At this point, no certificates are exchanged yet. -
Mutual Certificate Authentication
The RADIUS server sends its TLS certificate to the STA. Once verified, the STA returns its client certificate, which the server then authenticates. If both checks pass, the session is approved. -
Access Granted
The AP relays an EAP Success message, confirming successful authentication. -
4-Way Handshake
A secure encryption key exchange finalizes the session setup, ensuring data confidentiality on the Wi-Fi connection.
Common EAP-TLS Vulnerabilities and How to Mitigate Them
Username Disclosure
During the identity exchange, the STA may reveal a real username or device hostname, which can be used for reconnaissance.
Mitigation: Use EAP Identity Privacy to mask real usernames with pseudonyms during initial identity exchange.
Certificate Trust Issues
- Self-Signed Certificates: These are inherently insecure in EAP-TLS, as they lack third-party validation.
- Generic Third-Party Certificates: Often used in HTTPS, these may verify the issuer but not whether the certificate belongs to your specific network.
Mitigation: Deploy an internal Certificate Authority (CA) to issue and validate device certificates. This ensures devices only trust your infrastructure and reject rogue certs.
Real-World EAP-TLS Attacks: Device Exploits and Rogue Networks
Even with strong protocols like EAP-TLS, attackers typically go after the weakest link—the device.
Misconfigured Clients
Devices that fail to verify the server certificate or expose user identity are prime targets. An attacker can create a fake AP with a valid third-party certificate and trick poorly configured devices into connecting.
Rogue Network (Evil Twin) Scenarios
Many corporate devices automatically probe for known SSIDs like “NETGEAR” or “Corp-WiFi.” If an attacker sets up a fake AP with a matching SSID, a device may connect without user interaction.
Attack Chain:
- Device connects to rogue AP.
- Attacker performs MitM to inspect or modify traffic.
- Potential for credential theft, session hijacking, or malware delivery.
How to Secure EAP-TLS Deployments
- Enforce strict certificate validation on all client devices.
- Use EAP Identity Privacy by default.
- Deploy and manage an internal CA for certificate issuance.
- Regularly audit and test client device configurations.
- Educate users to recognize potential rogue network threats.
Final Thoughts
While EAP-TLS is one of the most secure authentication methods for enterprise Wi-Fi, attackers will always look for gaps—especially in client configurations. The best defense is a holistic security posture: enforce strict device settings, control certificate issuance, and monitor for rogue network activity.
Next Steps
Want to secure your enterprise Wi-Fi against EAP-TLS attacks?
Check out our wireless security training https://training.thexero.co.uk/p/wireless-mastery or join our Discord community for real-time support and updates.
